- Introducing VulnSec Platform
Detect, Analyze & Remediate Threats in Real-Time
External and internal vulnerability management with automated scanning, real-time monitoring, and actionable insights for modern enterprises.
How VulnSec Works
Get started with in three simple steps
Install the Vulnsec Agent
Quick setup with our lightweight agent for comprehensive system monitoring
Launch Internal or External Scan
Start automated vulnerability scanning with a single click
Get Real-Time Alerts & Reports
Receive instant notifications and detailed analysis of potential threats
Trusted by Cybersecurity Teams
Join hundreds of companies securing their infrastructure with VulnSec
Powerful Security Features for Modern Enterprises
Our comprehensive suite of security tools helps protect your digital assets from both external and internal threats.
Comprehensive Vulnerability Detection
Identify security weaknesses across your entire infrastructure with advanced scanning technology.
Asset Discovery & Management
Automatically discover and catalog all network assets to ensure complete visibility.
Risk Prioritization
Intelligently rank vulnerabilities based on severity, exploitability, and business impact.
Real-Time Threat Monitoring
Continuous surveillance of your systems with instant alerts when potential threats are detected.
Detailed Reporting
Generate comprehensive reports with actionable insights for stakeholders at all levels.
Compliance Monitoring
Stay compliant with industry standards including PCI DSS, HIPAA, GDPR, and more.

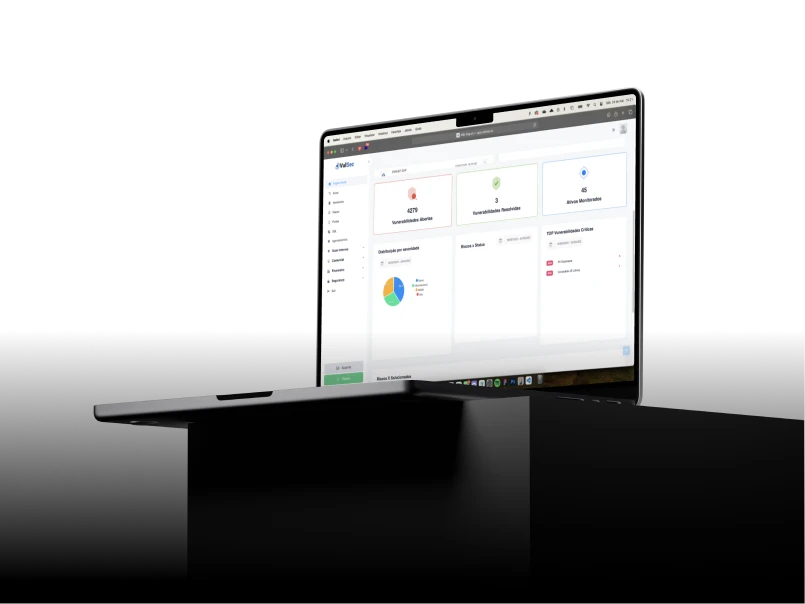
Real-time Security Intelligence Dashboard
Get a comprehensive view of your security posture with our intuitive dashboard that provides real-time insights and actionable intelligence.
Threat Detection
Advanced algorithms detect and classify security
threats in real-time.
Intuitive Dashboard
Clearly visualize metrics, reports, and scan history.
Performance Monitoring
Monitor system performance and security metrics with detailed analytics
Compliance Tracking
Track and maintain compliance with security standards
Automated Detection
Identify internal and external vulnerabilities using Nmap, ZAP, OpenVAS, and SSLyze.
Intelligent Prioritization
Risk- and severity-based classification with actionable insights.
Executive Reports & Actionable Insights
We generate detailed executive reports with actionable insights to help make fast and effective decisions about your digital infrastructure security.
Severity Classification:
Each vulnerability is automatically categorized into critical, high, medium, and low levels, facilitating action prioritization.
Executive Summary:
A clear and direct summary, ideal for executives and advisors, highlighting key risks and strategic recommendations.
Technical Insights:
A complete breakdown of each vulnerability, including evidence, technical descriptions, associated risks, and mitigation guidance.
Automated Recommendations:
Practical and prioritized suggestions based on recognized security frameworks such as OWASP, NIST, and MITRE ATT&CK.
History and Trends:
Comparative reports that show the evolution of security posture over time, helping identify trends and areas for continuous improvement.
Security Report
June 2025
Recommendation Summary
Critical patches required for 3 servers. Update framework dependencies to address injection vulnerabilities, Implement proper input validation for public-facing web forms.
VulnSec Features
VulnSec offers a wide range of features to help companies identify and remediate security vulnerabilities in real-time. Below are some of the key features offered:
1. External Application Scans
This functionality performs security tests on applications accessible via the internet, such as websites, APIs, or public web services. The goal is to identify vulnerabilities that could be exploited by external attackers, such as:
SQL Injection or XSS
Insecure configurations
Authentication/authorization failures
Outdated software (with known vulnerabilities)
Common tools: OWASP ZAP, WPScan
2. Internal Server Scans
Focused on identifying vulnerabilities in assets that are part of the company’s internal network (not publicly accessible), such as file servers, databases, and internal systems. Ideal for simulating attacks originating from within the corporate network or by attackers who have gained access to it.
Common tools: OpenVAS (run by an internal agent)
3. Port Scans
Identifies which ports are open on a server/device and what services are running on them. This is a crucial step in mapping the attack surface and detecting unnecessary or misconfigured services.
Examples of findings:
Open SSH with weak authentication
Insecure services (e.g., Telnet, FTP without encryption)
Common tool: Nmap
4. SSL/TLS Certificate Scans
Assesses the configuration of digital certificates used for secure communication (such as HTTPS). Detects issues like:
Expired or soon-to-expire certificates
Support for outdated and insecure protocols (e.g., SSLv3, TLS 1.0)
Weak ciphers
Vulnerabilities such as Heartbleed or POODLE
Common tool: SSLyze
Why use
VulnSec features?
Complete automation: recurring scheduling and automated reporting.
Comprehensive coverage: analysis of both the
external perimeter and internal infrastructure.
Smart alerts: real-time notifications about
critical vulnerabilities.
Practical recommendations: clear guidance on
how to fix each detected vulnerability.
- Limited Time Offer
Ready to Secure Your Digital Assets?
Start with a free vulnerability scan today and see how our comprehensive security platform can protect your business from emerging threats.
No credit card required. Full access to summary reports.
Vulnsec is a solution developed by Tcyber Solutions, a cybersecurity company with over 5 years of experience in the market. Our mission is to simplify vulnerability management through a platform that combines automation, intelligence, and continuous monitoring — for both internal and external environments.
By integrating industry-leading tools like OpenVAS, Nmap, SSLyze, WPScan, and OWASP ZAP, Vulnsec enables organizations to identify and address risks quickly, efficiently, and in a centralized way — from MVP stage to full-scale operations.
Products
Features
Vulsec – Internal and External Vulnerability Management Platform
Vulsec is a comprehensive vulnerability management platform designed to help organizations identify, analyze, and manage security risks across internal and external environments. It combines automated scanning engines, agent-based scanning, and a centralized dashboard to simplify cybersecurity operations.
🧠 Key Features
1. Automated Vulnerability Scanning
External Scans: Regular scans of public-facing assets using tools like Nmap, OWASP ZAP, SSLyze, and OpenVAS.
Internal Scans: Conducted by a lightweight agent installed on a single host inside the client’s network, scanning the entire IP range for vulnerabilities.
2. Agent-Based Internal Discovery
One agent per client network, no need for multiple installations.
Scans all internal devices from a central point.
Detects open ports, outdated software, misconfigurations, and other weaknesses.
3. Vulnerability Database & Classification
Leverages CVE (Common Vulnerabilities and Exposures) data.
Classifies findings by severity (Critical, High, Medium, Low).
Includes CVSS scores and technical details.
4. Interactive Dashboard
Centralized management of all vulnerabilities.
Filter results by date, severity, asset, or scan type.
Visual graphs to track remediation progress and risk posture over time.
5. Ticketing & Workflow
Assign vulnerabilities to responsible team members.
Track remediation progress with status updates.
Export tickets to third-party systems (future integration roadmap: Jira, ServiceNow, etc.).
6. Scan Scheduling & Customization
Schedule recurring scans (daily, weekly, monthly).
Customize scan profiles to include/exclude specific ports, services, or IP ranges.
7. Reporting & Compliance
Generate PDF and CSV reports.
Executive and technical reports.
Supports compliance with standards like ISO 27001, NIST, and GDPR (via evidence of continuous monitoring).
8. Email Notifications & Alerts
Real-time alerts for critical vulnerabilities.
Notification system for completed scans and remediation deadlines.
9. User & Role Management
Role-based access control (RBAC).
Admins, analysts, and read-only user roles.
Audit logs of all user actions.
10. Data Security & Privacy
Data encrypted at rest and in transit.
The agent does not store sensitive data – only scan metadata and findings.
🛠️ Technology Stack
Backend Engines: Nmap, ZAP, SSLyze, OpenVAS
Frontend: Web-based dashboard with responsive design
Agent: Lightweight Linux agent
Architecture: SaaS or on-premises options available
Use cases
Vulnsec Use Cases
1. Internal Vulnerability Scanning
Description: Detection of vulnerabilities within internal network devices.
Tools Used: Nmap, OpenVAS, SSLyze, OWASP ZAP.
Benefits: Identifies weaknesses before attackers do, focusing on servers, workstations, routers, etc.
2. External Vulnerability Scanning
Description: Analysis of internet-exposed assets (DNS, web applications, public IPs).
Tools Used: OWASP ZAP, SSLyze, Nmap.
Benefits: Secures web apps, exposed servers, and other public-facing assets against external threats.
3. Automated Executive & Technical Reports
Description: Generation of detailed technical and executive-level reports (risk score, CVSS, recommendations).
Target Audience: IT teams, CISOs, auditors, and management.
Benefits: Facilitates communication with stakeholders and improves understanding of critical vulnerabilities.
4. Vulnerability Prioritization
Description: Automated ranking based on severity (CVSS score, exploit availability, external exposure, etc.).
Benefits: Focuses efforts on the most dangerous and likely-to-be-exploited vulnerabilities.
5. Continuous Vulnerability Management
Description: Scheduled re-scans and tracking of remediation progress.
Benefits: Maintains ongoing security posture and detects new risks as environments evolve.
6. Compliance and Audit Readiness
Description: Supports compliance with standards like ISO 27001, PCI-DSS, LGPD, etc.
Benefits: Ensures readiness for audits and avoids fines or regulatory issues.
7. Security Maturity Tracking
Description: Historical tracking of resolved vulnerabilities and risk reduction over time.
Benefits: Visual metrics to demonstrate improvements in cybersecurity posture.
8. Integration with Tcyber Professional Services
Description: Optional integration with Tcyber’s team for remediation and incident response.
Benefits: Companies without in-house security teams can get expert support on demand.
9. Use by Security Consultants and MSSPs
Description: Consultants and MSSPs use Vulsec to manage vulnerabilities across multiple clients.
Benefits: Multi-tenant support, white-label reporting, and scalability for service providers.
10. Network Misconfiguration Detection
Description: Alerts for unnecessary services, open ports, outdated protocols.
Benefits: Enhances network hygiene and reduces attack surface.
Enterprise
About us
Vulnsec is a solution developed by Tcyber Solutions, a cybersecurity company with over 5 years of experience in the market. Our mission is to simplify vulnerability management through a platform that combines automation, intelligence, and continuous monitoring — for both internal and external environments.
By integrating industry-leading tools like OpenVAS, Nmap, SSLyze, WPScan, and OWASP ZAP, Vulnsec enables organizations to identify and address risks quickly, efficiently, and in a centralized way — from MVP stage to full-scale operations.
